Whiteboxcrypto |
WBC: protecting cryptographic keys in software applicationsCryptography is increasingly deployed in applications that are executed on open devices (such as PCs, tablets or smartphones). The open nature of these systems makes the software extremely vulnerable to attacks, since the attacker has complete control over the execution platform and the software implementation itself. This means that an attacker can easily analyse the binary code of the application, and the corresponding memory pages during execution; the attacker can intercept system calls, tamper with the binary and its execution; and use any kind of attack tool such as IDA Pro, debuggers, emulators, etc. Such an attack context is denoted as the white-box attack context.
The challenge that white-box cryptography aims to address is to implement a cryptographic algorithm in software in such a way that cryptographic assets remain secure even when subject to white-box attacks.
Therefore, white-box cryptography (WBC) is an essential technology in any software protection strategy. This technology allows to perform cryptographic operations without revealing any portion of confidential information such as the cryptographic key. Without this, attackers could easily grab secret keys from the binary implementation, from memory, or intercept information that would lead to disclosure at execution time. WBC could be seen as a special purpose code generator that turns a given cipher into a robust representation. A representation where the operations on the secret key are combined with random data and code, in such a way that the random data cannot be distinguished from key information. The figure below depicts a conceptual high-level overview of WBC, for the case of a fixed key implementation. In such an implementation, the key will be hard-coded into the code. On the left hand side is the description of a cryptographic cipher and the key. White-box transformations will then generate the code for an application that is semantically the same, but for which it is hard to extract the key that is embedded into the code. 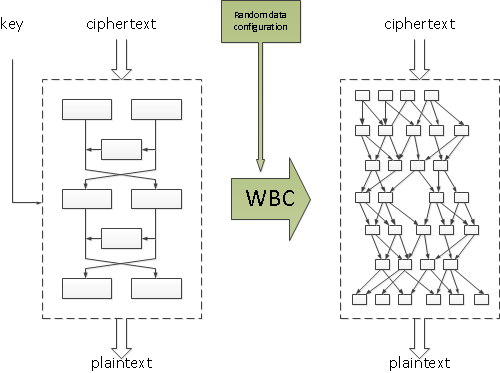
This website aims to introduce the topic of white-box cryptography to the interested reader, and aims to encourage academic research. A recent introduction on white-box cryptography can be found here: |
|
|